7 Trends Daily
Stay updated with the latest insights and trends across various sectors.
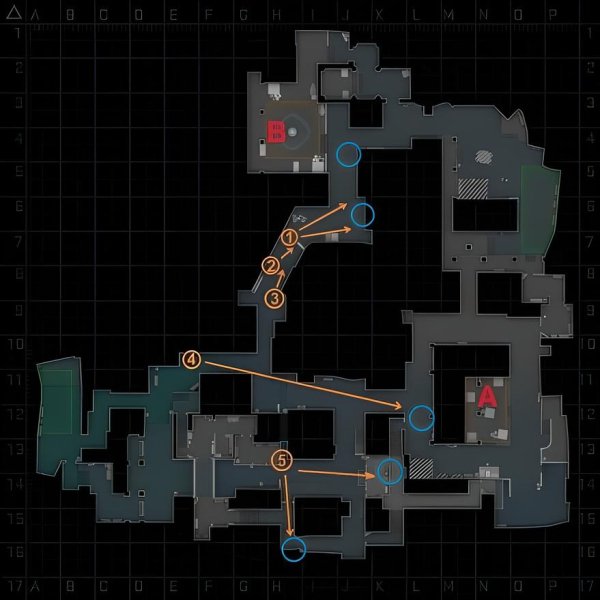
CT Setups That Make Terrorists Cry
Discover jaw-dropping CT setups that will leave terrorists in tears. Unlock strategies to dominate your games now!
Top 5 CT Setups That Dominate As Terrorists Approach
When it comes to dominating the battlefield in competitive Counter-Strike: Global Offensive, having the right CT setups is crucial, especially as terrorists approach. Here are the top 5 CT setups that consistently prove effective:
- **A Site Crossfire**: Positioning one player in the balcony and another in the site itself creates a deadly crossfire, allowing for multiple angles of attack against unsuspecting terrorists.
- **B Site Back Bombsite**: A player hiding behind the bombsite box can catch incoming players off-guard, while a teammate can hold an angle in the site for support.
- **Mid Control Setup**: Use of utility to smoke and blind enemies rushing mid allows the CTs to take control and gather information, making it easier to rotate quickly.
- **Jungle and Connector Hold**: Two players holding this crucial area can cover multiple paths, maintaining a strong defensive line against terrorists.
- **Aggressive Push on Eco Rounds**: When saving, aggressive positioning in choke points can yield high reward, catching terrorists off-guard and securing weapons for the next round.
Mastering these CT setups not only increases your chances of winning rounds but also hones your team's coordination. Understanding when to rotate and how to utilize utility effectively can turn the tide during intense engagements. It's essential to communicate with your team to adapt these setups to counter the terrorists' strategies, ensuring you stay one step ahead in the game.
Counter-Strike is a popular first-person shooter game that pits teams against each other in tactical combat. One of the interesting aspects of the game is the variety of skins and cases players can collect, such as the Gamma Case, which contains various weapon skins that players can use to customize their gameplay experience.
How to Create Unbeatable CT Defenses: Strategies That Work
In today's competitive landscape, creating unbeatable CT defenses requires a multifaceted approach that incorporates both technology and human expertise. Start by conducting a thorough risk assessment to identify vulnerabilities within your current defense framework. This step is crucial as it allows you to prioritize areas that need immediate attention. After you have pinpointed these vulnerabilities, implement the following strategies:
- Utilize advanced threat detection systems that leverage AI and machine learning for real-time monitoring.
- Regularly update your security protocols to stay ahead of emerging threats.
- Conduct penetration testing to evaluate how well your defenses hold up against simulated attacks.
In addition to technology, fostering a culture of security awareness within your organization is vital for maintaining unbeatable CT defenses. Employees often unknowingly become the weakest link in security protocols. Therefore, it is essential to provide regular training sessions on identifying phishing attempts and understanding the importance of strong password practices. Furthermore, consider implementing a multi-factor authentication (MFA) system to add an extra layer of protection. As a result, a well-informed team combined with robust technical solutions will significantly enhance your organization's resilience against cyber threats.
What Makes a CT Defense Setup Effective Against Terrorist Tactics?
An effective counter-terrorism (CT) defense setup hinges on several key components that work synergistically to thwart terrorist tactics. Intelligence gathering is paramount; this includes real-time surveillance, informant networks, and data analysis to predict potential threats. Secondary to intelligence, community engagement plays a crucial role in building trust and cooperation between local populations and law enforcement agencies. When communities feel empowered, they are more likely to report suspicious activities, which can significantly enhance the overall security posture. Integrating these elements with advanced technology, such as AI-driven monitoring systems and biometric recognition tools, offers a robust framework for quick assessment and response.
Furthermore, an effective CT defense setup requires comprehensive training and preparedness for first responders. This involves conducting regular drills and simulations to ensure that all personnel are familiar with both protocols and the latest terrorist tactics. Additionally, establishing a clear command and communication structure allows for better coordination during a crisis. As part of a holistic approach, international collaboration is essential, as terrorism is often a global issue. Sharing intelligence, techniques, and best practices among nations not only strengthens each country's defenses but also contributes to a unified front against terrorist threats.